How does a captive portal work? Here are the basics.
The captive portal is also known as captive portal login.
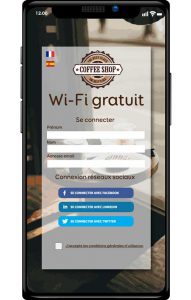
The principle of the captive portal is to allow a person to connect to a Wi-Fi network, under the condition of providing identifiers (e-mail, name, first name…).
During the identification, the user is redirected to a web page with normally a form to fill. This automatic redirection to the portal is called Catch and Release.
Captive portals also have an opt-in/check box to indicate acceptance of the terms and conditions of use. This is essential, especially in the context of the General Data Protection Regulation (GDPR).
How the Captive Portal works
A portal can have several functions. Here is the main model:
- A visitor starts to connect to a network.
- The DCHP, or Dynamic Host Configuration Protocol, assigns an Internet Protocol host and an address (IP).
- The firewall, or gateway, prevents access to the Internet.
- Only one port (80) leads the user to a web page by having him open his web browser.
The web page in question is the captive portal in which you must enter your information, in addition to accepting the terms of use.
The advantages of the Captive Portal

For companies and communities, a captive portal brings interesting advantages:
- A legal obtainment of users’ data.
- Better understand the profiles of the connected people.
- Gather data (ages, connection times, visited sites, most viewed messages…).
- Opportunities to put forward adapted offers and products.
- Bandwidth limitation if the city or organization wants to control costs.
- There is also personalized marketing to be deployed on efficient channels, from the captive portal for example. This is what we call Wi-Fi Marketing.
How is a Captive Portal created?

There are several tools for creating a captive portal. ADIPSYS allows you to easily create one, with advanced functions and customizable templates, thanks to our HOTSPOT MANAGER solution.
With our captive portal management system:
- You are compliant with CNIL and RGPD legislation.
- Your captive portal is ergonomic and responsive, adapted to mobiles and tablets.
- Visitors have an optimal browsing experience.
- You obtain user data in compliance with the law.
- Our solution brings you rich usage statistics.
Find our tips for choosing a Captive Portal and securing Wi-Fi
The creation of a captive portal allows you to considerably secure your Wi-Fi network. In this article we explain how the captive portal works, and how it can make users’ connection more secure.
Did you like this article? Read new articles every week on our LinkedIn page. Follow us to stay up to date with the latest trends in the Wi-Fi hotspot market and click on the logo below to follow us.
For more information on our solutions, please contact us at sales@adipsys.com.
